What we are doing
Posted December 22, 2021 by Sun ‐ 5 min read
As we all know, the industry we are in has never lacked fancy concepts, web3/metaverse/?? As a gimmick, we are in a storm, and we are inevitably lost. In order to be able to see the way forward, I would like to summarize it, and we will sort it out from two points: one is the original intention; the other is the current projects, progress and plan.
1. the original intention
What is the ultimate dream of a person living?
Immortality.
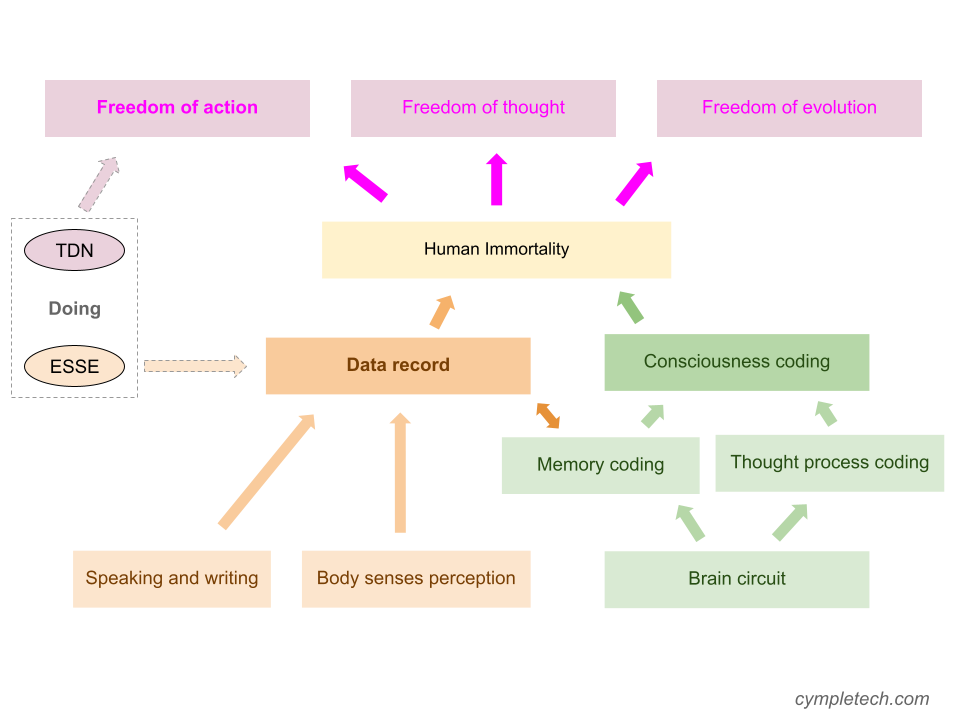
In short, there are two elements that make up human beings: human flesh and human consciousness. Immortality is nothing more than starting from these two directions, either by transforming the body, modifying genes, so that cells can maintain vitality and even regenerating; or by continuing consciousness and giving consciousness a carrier so that it can survive forever. The former may be possible, but it cannot be applied on a large scale, because if everyone can live forever, the demand for resources by the increasing population will be unpredictable, even if they can move to extraterrestrials, even if they can regenerate resources, The “population bomb” will always become a potential hazard. From another perspective, this plan also needs to be accompanied by high late-stage investment. Is it affordable for the people?
The latter solution-continuation of consciousness, relatively, the cost of technical replication is low, and the subsequent maintenance cost is low, and it is more likely to become an immortal solution that everyone can afford and enjoy.
So what are the foundations for continuation of consciousness? I think it can be divided into: “consciousness of the now” and “consciousness of the past”. “Consciousness of the now” is our ability to respond accordingly to the stimuli in the current real life based on the accumulation of experience. This area is mainly the study of the brain’s operating mechanism, related research such as “brain-computer interface”, etc. It is also underway, and I believe there will be a chance to achieve it someday in the future, so I will not discuss it for now. “Consciousness of the past” includes all kinds of information we input and output in the past. The input information includes the physiological information received by our body sense organs (nerves, muscles, skin, etc.), every book we have read, every movie we have seen, every song we have heard, and other cultural information; the output information includes all the information we publish to the outside world, such as every voice, every photo, every circle of friends, every movie comment, music comment, and even swear words. This information is now also in the form of data, which is the “part of me” compiled by digital signals.
I don’t know if you have watched “Black Mirror”. The first episode of the second season tells a story based on the text, photos, videos and other information posted on the Internet by the deceased. The story of the “rebirth” to accompany the lover. The basis of this “rebirth” is the “output information” I mentioned earlier. In contrast to real life, I realize that all the content I output is controlled by the platform, and the platform can use and delete the content I output at will. That is to say, the “this part of me” compiled by digital signals does not belong to me. So if the technology is mature enough, can the platform that owns my data copy me at will? (make me afraid).
2. the progress and planning of the current projects
Therefore, I want to make a series of attempts based on my own “data ownership”, hoping to build a secure data environment for everyone and provide a possibility to truly control their own data. My place, my rules.
ESSE: Provides data visualization and interactive entry. With a friendly interface for ordinary users, it transforms abstract data concepts into software that everyone can actually experience. It has been preliminarily constructed, with practical functions including peer-to-peer chat, groups, notes, wallets, etc.
TDN: Build a secure data transmission network channel. Including P2P network, local network, centralized network, overlay network, proxy and relay services, etc. Most of them have been constructed and put into actual use.
PDS: Build a safe data storage place. Including local encrypted storage of data, personal multi-device synchronization, encrypted cloud storage, decentralized storage, etc. It is currently under construction, and some have been actually used.
PDC: Build a safe data processing method. Including all aspects of data processing, the readable, writable, changeable, deletable, safe calculation of the data, etc. Currently, under construction.
PDE: Build a safe way to share data. An ability to authorize others to use their own data, including safe and reliable exchange of data, share data, etc. It is also currently under construction.
For the data privacy, for the sustainability of consciousness, we are striving to move forward. Happy Hacking!